Datenschutz & Sicherheit
Databroker Files: Targeting the EU

This is a joint investigation with Bayerischer Rundfunk, L’Echo (Belgium), Le Monde (France), BNR (Netherlands). It is part of the “Databroker Files”. A German version of this article was published under the title „Datenhändler verkaufen metergenaue Standortdaten von EU-Personal“.
There are detached houses with front gardens in an upmarket district of Brussels, and the political centre of the European Union is not far away. When they are out and about early in the morning, a top EU official only needs about 20 minutes by car to get to their workplace. They work in a unit under the authority of Commission President Ursula von der Leyen at the Berlaymont building, the European Commission’s headquarters. Conveniently, there’s a spa and fitness centre along their way to work – they have passed by it, too.
We know this and more because we have their exact location data. The data even tells us exactly where their office is in the EU Commission building. We discovered their movement patterns, along with those of millions of other Europeans, in commercially traded data.
This data reveals where people live and work, as well as their behaviour and preferences. It can also show visits to clinics, religious buildings, party and trade union headquarters, as well as brothels and swingers‘ clubs.
The investigative team has data records from several data brokers. They are giving these away as a sample — a free preview of what is on offer with a paid subscription. For this investigation, we analysed two new datasets containing around 278 million records of mobile phone locations in Belgium.
Danger of espionage like during the Cold War
Almost ten years ago, a revolution with four letters took place here in Brussels: GDPR. In December 2015, the European Parliament, the Council and the European Commission agreed on the text of the General Data Protection Regulation. It was intended to harmonise the protection of fundamental rights in the digital world with a data-based economy. And it came with the promise of informational self-determination: that people should generally have sovereignty over who does what with their data.
This promise remains unfulfilled to this day. Instead, the Databroker Files reveal an unprecedented loss of privacy that can affect all people who participate in digital life by using apps on smartphones or tablets. The uncontrolled data business is no longer just an issue of consumer and fundamental rights protection; it also poses a threat to Europe’s security.
The risk of espionage in the EU is high, at least since Russia launched its large-scale war of aggression against Ukraine in February 2022. Authorities warn of Russian sabotage suspicious drones violate European airspace, a Chinese spy infiltrated the EU Parliament – hardly a month goes by without a new espionage scandal. Back in 2020, the then president of the German domestic intelligence service compared the situation to that of the Cold War.
Those responsible have apparently not yet sufficiently recognised the extent of the danger posed by commercially collected data in this context. When confronted with the results of our research, the EU Commission stated: „We are concerned with the trade of geolocation data from citizens and Commission officials.“ The Commission has now issued new guidance to its staff regarding ad tracking settings on both corporate and private devices. It has also informed other Union entities and Computer Security Incident Response Teams (CSIRTs) in Member States.
In response to this investigation, members of the European Parliament (MEP) are demanding decisive action. „In view of the current geopolitical situation, we must take this threat very seriously and put an end to it,“ writes Axel Voss (CDU) from the conservative EPP group. Lina Gálvez Muñoz, a Spanish MEP from the Socialist Group S&D, calls for the EU to treat the issue „as a priority security threat, not just a privacy concern“. With regard to the military threat posed by Russia, German MEP Alexandra Geese (Greens/EFA) demands: „Europe must prohibit large-scale data profiling.“
Hundreds of potentially sensitive employees targeted
Our investigation shows how easy it is to spy on top EU staff using commercially traded location data. Based only on the preview data sets available to us, and without paying a cent, we were able to spot hundreds of devices belonging to people working for the European Union in sensitive areas. In the EU Commission headquarters alone, there were around 2,000 location pings from 264 different devices. In the European Parliament, there were around 5,800 location pings from 756 devices.
For example, a movement profile illustrates the daily commute of an EU Parliament employee. They travelled from a community near Brussels to the city centre via the urban motorway. The tracking shows how the employee visits several buildings of the EU Parliament, a supermarket and a restaurant.
Furthermore, we found thousands of location pings in various other institutions, ranging from the Council of the European Union to the European External Action Service and the European Data Protection Supervisor. The preview data sets used for this analysis are just the tip of the iceberg. Paid subscriptions promise large-scale mass surveillance with a constant supply of up-to-date location data.
Even with this limited data, we were able to identify the private addresses of five individuals who work or have worked for the EU, including three people in senior positions. Among the EU staff we identified are a the top Commission official mentioned at the beginning, a high-ranking diplomat from an EU country, and employees of the EU Parliament and the European External Action Service. Initially, they were all suspicious when we contacted them. Some preferred to speak to us only briefly or not at all. None of them wanted to be quoted publicly. Two of the individuals in question confirmed to us that the location data indeed shows their place of residence and workplace, as well as their movements in Brussels. We also found a digital rights activist and a journalist in the data, who confirmed its accuracy.
The data travels along winding paths through an opaque ecosystem, beginning with apps that claim to only track users for advertising purposes. Ultimately, it ends up in the hands of data brokers, and, potentially, anyone who asks for it. These could be advertising companies, journalists – or even foreign intelligence services.
Location data is not anonymous
The data sets offered by data brokers do not contain the names or addresses of mobile phone users who are tracked at every step. Nevertheless, we were able to identify several individuals. This was made possible, among other things, by the so-called Mobile Advertising ID, which is a unique identifier for the online advertising industry that Google and Apple automatically assign to each phone.
Each location in our data sets is linked to such an ID. This allows loose data points to be combined to form detailed movement profiles. Places of residence and work can easily be identified because locations are noticeably concentrated here. Particularly in the case of freestanding houses with publicly visible doorbell signs, it quickly becomes clear whose location data is involved. In some cases, the residents of a house can also be identified online, for example in the telephone directory or through the imprint on their website. Our investigation proves that location data is not anonymous.
Reactions to the Databroker Files in political Brussels are often characterised by surprise or nervousness. Even high-ranking employees responsible for data protection and digital regulation would not have expected the precision of openly traded mobile phone location data.
Urgent warning from NATO
NATO also has its headquarters in Brussels. In our sample data sets alone, there are 9,600 mobile phone location pings on NATO premises, recorded by 543 different devices. The alliance is under extraordinary pressure due to the tense military situation and Russian espionage, among other things. What is its response to the findings of our investigation?
„We are fully aware of the general risks that third-party data collction poses to the Alliance“ writes a NATO representative in French. Measures had been taken to mitigate these risks – but when asked, he would not explain what they were.
The fact that the military alliance apparently perceives such cell phone tracking by the advertising industry as a threat is demonstrated by the urgent request made by the NATO representative to the reporters. „We take the security of our staff very seriously, and trust that you will do your utmost not to publish any information that could harm them,“ he writes. „It is essential that no telephone located at NATO headquarters be identified or associated with named persons, and that no telephone linked to NATO be located in any other place.“
The Belgian military also responded to our research after L’Echo’s team discovered movement profiles on Belgian military sites. „We are fully aware of the problem,“ says the press office. The use of private devices is often already prohibited, but not in military quarters. They are working on a new directive that strongly advises personnel not to use applications that allow conclusions about their place of residence or workplace. However, our investigation shows that location data can potentially leak via almost any app
Wir sind ein spendenfinanziertes Medium
Unterstütze auch Du unsere Arbeit mit einer Spende.
What intelligence services can do with advertising data
Several years ago, a study by the NATO research centre Stratcom (Strategic Communications Centre of Excellence) highlighted that such data poses a threat not only to our privacy, but also to military security. With the help of such data, enemy actors would be able to identify and spy on key military personnel or track military operations.
Neither NATO nor the EU or its member states have been able to find an antidote since then. In 2024, together with Bayerischer Rundfunk, we analysed commercially traded location data from Germany to demonstrate how it can be exploited to identify and spy on high-ranking government officials, as well as members of the military and intelligence services. Using the data, the most important US and NATO bases in Germany could also be spied on. It even revealed visits to brothels. We obtained the data from a US data broker, mediated through a Berlin-based data marketplace.
Similar journalistic investigations from European countries such as the Netherlands, Norway and Switzerland have also proven the problem. The new research by our partner L’Echo today demonstrates how vulnerable Belgium is due to openly traded location data. Police forces, prisons and critical infrastructure, such as nuclear power plants, can be spied on.
The dangerous business of advertising intelligence
If the investigative team was able to target high-ranking EU personnel with just two free data samples and these simple methods, what could well-resourced intelligence services or other malicious actors achieve with commercially available data?
In recent years, a new branch of the global surveillance industry has emerged. It specialises in making data from the online advertising ecosystem available to government agencies. The US company Babel Street, for example, claims to have developed a kind of „Google Maps for mobile phones“ with its service Locate X. The system is said to allow law enforcement agencies to easily track down individuals.
The technical term for this is „ADINT“, which stands for Advertising Based Intelligence. The dangers posed by ADINT, for example from foreign intelligence services, can be described as hybrid threats. This term describes attacks that are not overtly military in nature, such as espionage or sabotage.
Researchers warn: „Extremely worrying“
At the Helsinki-based research centre Hybrid CoE, experts from several disciplines are conducting research on behalf of the EU and NATO into defending against hybrid threats. Regarding the results of our investigation, spokesperson Kiri Peres writes: „Mobile location data could be exploited by hostile actors to facilitate hybrid activities to harm the democratic society and undermine the decision-making capability of a state.“
As Peres explains, it seems „only logical“ for China and Russia to acquire data from the advertising industry. It could be used, for example, to track people who oppose the regime or attend mass protests. High-ranking individuals abroad could be identified and spied on, including politicians and journalists, members of the government, the military, and the secret services. In wartime, data from the advertising industry could be used to track military movements.
Corbinian Ruckerbauer researches surveillance and digital rights at the non-profit think tank interface in Germany. When asked by netzpolitik.org, he expresses considerable doubt that European intelligence services and security authorities are truly aware of the threat posed by mobile phone location data from the advertising industry.
„Neither do government agencies nor parliamentary committees publicly discuss such threat scenarios, nor is there any discussion of what contribution we Europeans would actually have to make in order to tackle this problem in a sustainable manner“, writes Ruckerbauer. He adds that EU states „should develop legal solutions and enforcement mechanisms to restrict this sprawling data market“.
His colleague Thorsten Wetzling from interface writes: „Especially at the current time, when the European security and defence landscape is being tested daily by Russia for possible attack vectors, it is extremely worrying that sensitive location data can still be acquired so easily on the data market to such an extent.“
However, it is worth noting that Western intelligence services and other government agencies are also reportedly using data from the advertising industry. In the USA, their services are used by the ICE deportation troops authority, among others.
In the jungle of data brokers
But how does this data end up in the hands of these companies in the first place? Our previous investigations habe given us unique insights into the depths of the data industry. In our explanatory article, we compare the tangled paths of the data trading ecosystem to a jungle.
It all starts with apps that people give permission to, either consciously or unconsciously, to collect their location data. In order to monetise their services, developers either embed code from tracking companies directly into their apps or offer advertising space to third parties. By doing the latter, they broadcast extensive information about their users to dozens or even hundreds of companies that participate in auctions, bidding for the opportunity to display ads to their target groups. Some use this data not only for advertising purposes, but also as a commodity – which is a tempting offer for data brokers.
The quality of the data varies. Data brokers sometimes present their data sets as larger than they really are, for example by adding fake advertising IDs to real location data. It is therefore possible that the data records available to us with 2.6 million different advertising IDs are actually based on fewer than 2.6 million different devices. Nevertheless, our investigation shows how individuals and institutions can be targeted even with inaccurate data.
The Databroker Files also reveal that many European companies are heavily engaged in the data industry. A data marketplace called Datarade, for example, is an important infrastructure for the industry. It is based in Berlin. Meanwhile, our conversations with developers show that they are often unaware of who their apps share users‘ data with. What they do notice, is the increase in revenue when the number of users increases, whether through payments from tracking companies or advertising revenue.
What tracked people in Brussels say
Only two individuals from our dataset are willing to publicly share their perspective. However, neither of them is employed by the EU. The first is Shubham Kaushik, who works for European Digital Rights (EDRi), an umbrella organisation for digital rights organisations. She volunteered her advertising ID to us – score. She says:
„It felt really invasive. Without my knowledge, personal information about me is out there for anyone with money to buy and access.“. The only way to preserve people’s right to privacy and live their lives freely is to ban the tracking industry.“
Only a single location ping of Kaushik appears in our data records. In contrast, a journalist from the Belgian newspaper L’Echo was tracked several times. The location data showed where he lives and where he had been on holiday. He says:
„I make efforts not to be tracked, but apparently they are not enough. Imagine if I were a journalist writing about China – and China could track and spy on me.“
Data protection as a race to the bottom
How is all this possible when the EU has the General Data Protection Regulation in place? This question shakes the very foundations of the European self-image. Through its comprehensive digital regulation, the European Union has sought to demonstrate how it can democratically shape the digital world by finding a fair compromise: Economically oriented forces got a regulation that did not contain any harsh prohibitions, but merely rules and guidelines for data processing. Fundamental rights orientated forces obtained individual rights, such as the right to information or deletion of data, as well as strengthened supervisory authorities.
Much of this is held together by the instrument of consent. It is the legal basis for many cases of data processing and is intended to give people freedom of choice. Particularly when it comes to data processing for apps and online services, the idea was that people do not actually have to consent – but they can, as long as they are informed and do it voluntarily.
The idea was that this would lead to a competition and a race to the top, resulting in only trustworthy providers receiving consent. In the words of the the EU Commission: „Data protection as a competitive advantage“. In practice, however, it has become a race to the bottom, with companies doing everything they can to collect as much consent as possible. They trick users with manipulative design or simply give them no choice but to consent to tracking. The Databroker Files are a direct consequence of this competition for the worst data protection.
Illegal on paper
On paper, there is little doubt among data protection experts that the data broker business we have uncovered is illegal. This view was expressed, for example, by the Federal Data Protection Commissioner of Germany, Louisa Specht-Riemenschneider.
The problem begins with the issue of consent. According to the unanimous legal interpretation of data protection authorities, consent is the only legal basis on which advertising tracking can be based. In addition to the aforementioned problems with voluntariness, the main issue here is that the consent is often not informed. For instance, anyone who has agreed to the privacy policy when installing a weather app would not be able to understand where their data ends up, especially if it is being traded freely.
This also undermines the rights of data subjects, since they cannot make requests for information or deletion to companies they are not familiar with. In addition, location data can reveal sensitive personal information that is specially protected by the GDPR. This could include location tracking in rehab clinics, religious buildings, party and trade union buildings or queer sex clubs, for example.
Another issue is the purpose limitation, a principle of the GDPR, according to which data may only be used for the purposes for which it was collected. However, with data brokers, data that is allegedly only collected for advertising purposes becomes a commodity without a more precisely defined purpose. According to data protection experts, this constitutes a clear violation.
The problem of GDPR enforcement
There are two related reasons why the authorities have not taken stronger action against the system of advertising tracking and data trading. Firstly, the authorities only tend to take action when they receive complaints from citizens, and citizens can only complain about companies they know. This is why there are so many complaints about faulty cookie banners, but not about the invisible infrastructure behind them. Tracking companies have made themselves comfortable in the shadow of the GDPR, which is why Irish data protection activist Johnny Ryan coined the term „data protection free zone“ for everything that happens behind the cookie banner.
Secondly, European data protection authorities are often still inadequately equipped. They receive so many complaints from citizens that they have hardly any resources left for conducting strategic ex officio investigations. Additionally, the authorities are primarily legally equipped and lack the technical expertise and personnel required for more complex analyses.
In Germany, our reporting has triggered first investigations and consequences from state data protection authorities. However, the Data Protection Commissioner of Berlin, Meike Kamp, is also calling for legislative support to get the systematic problem under control. According to her, “clearer statutory regulation of online tracking and profiling” would be “desirable.”
Her colleague Bettina Gayk from North Rhine-Westphalia says that, as a data protection authority, she can only take action in individual cases. “A truly comprehensive impact could only be achieved by a legal ban that precisely defines permissible processing of location data for specific purposes, tightly limits it, and fundamentally prohibits any personal or identifiable onward sharing of the data.” She warns that location tracking in hospitals or at political events, for example, can reveal particularly sensitive data. “This kind of thing must never become a commodity.“
From the siding to the graveyard
Can the European Union muster the strength for further digital regulation in the current situation? Laws such as the AI Act, the Digital Services Act and Digital Markets Act are under massive pressure from companies and countries within and outside Europe. When discussing a reform of the data protection, it is almost always just about making things easier for businesses.
This spring, the EU Commission buried a proposed regulation intended to solve the problem of consent online, after years of stagnation. The ePrivacy Regulation was actually due to be adopted in 2018 to supplement the GDPR, which came into effect that year. Had the EU Parliament had its way, users would have been able to decide centrally, in their browser or smartphone operating system, whether and by whom they wanted to be tracked. This decision would have been legally binding.
The prospect of users actually being able to decide who receives their data online caused sheer panic in the data industry. Online advertising companies, Silicon Valley corporations and time-honoured European media companies joined forces in a broad alliance to prevent the regulation. They compared it to a nuclear bomb for the internet and warned of the end of free – meaning ad-financed – journalism on the internet.
With success: Under the constant fire of their lobbying initiatives, the project was pushed further and further onto the back burner. Although the European Parliament adopted an ambitious draft in 2018, the member states were unable to reach an agreement in the Council for years. In spring 2025, the EU Commission finally withdrew the proposed regulation.
The Digital Fairness Act gives little hope
The EU Commission has vaguely promised a follow-up initiative, but it is uncertain whether it will actually materialise. First up is the Digital Fairness Act, which Commission President Ursula von der Leyen first announced at the start of her second term of office.
The law is intended to close gaps in digital consumer protection. The Commission collected feedback on this in a public consultation until October; the wish list of possible regulations is long. It remains to be seen whether the problem of consent, advertising tracking and data trading will be included.
Parliamentary circles say that hopes should not be too high. It is considered unlikely that comprehensive regulation will be put on the agenda in the current political climate, in which reducing bureaucracy is the order of the day.
Civil society organisations such as the Chaos Computer Club and the Federation of German Consumer Organisations are calling for an approach that tackles the root of the problem head on: a blanket ban on advertising tracking and data trading.
In fact, there was already a cross-party initiative in the EU Parliament in 2020 that aimed to achieve just that. The „Tracking-Free Ads Coalition“ wanted to enshrine a corresponding ban in the Digital Services Act (DSA) being negotiated at the time, but failed to gain a majority in favour. Today, the DSA only prohibits targeting with data relating to minors and sensitive data, such as religion, sexuality, health or politics.
MEP: „Ban tracking completely“
In response to our investigation, the European Commission prefers not to talk about new regulation. „We already have put strong legislation in place in the EU, namely the GDPR,“ writes a spokesperson. He states that it is a matter for the national supervisory authorities, including the national data protection authorities, to determine whether EU data protection laws have been breached. „The Commission stands ready to cooperate with those authorities.“
Axel Voss, a German digital politician from the conservative EPP group in the EU Parliament, believes the EU should take decisive action in light of the investigation. „We need a more precise definition of the use of location data and therefore a clear ban on trading particularly sensitive location data for other purposes“. For reasons of data protection and security, he believes that „strict restrictions are necessary, especially where movement or behavioural data allow conclusions to be drawn about sensitive areas“. The aim must be to „protect citizens and security interests without unnecessarily burdening European companies“.
Voss also calls for „a Europe-wide registration obligation for data traders and consistent enforcement of existing data protection rules“. In contrast, he is cautious about a comprehensive ban on tracking and profiling for advertising purposes: „A complete ban is a far-reaching step that needs to be carefully considered.“ However, it must be clear that location data should not be treated as an „economic object“.
Spanish MEP Lina Gálvez Muñoz commented on the research on behalf of the Socialist Group S&D in the EU Parliament. With regard to data trafficking, she writes: „In a context of escalating geopolitical tensions, this poses direct threats to national and collective security.“ The EU has „a good legal framework as a starting point,“ she continues, citing the Cyber Solidarity Act and the Cybersecurity Act as examples. „We need to keep working on strengthening and adapting it to the current geopolitical context as well as on implementing and enforcing it.“ Gálvez Muñoz also believes that the EU needs to expand the scope of the existing legislation.
Alexandra Geese, a German MEP from the Green Group, reiterates the call for a ban on tracking and profiling for advertising purposes. „I have championed such a prohibition for years,“ writes Geese. „Detailed knowledge about individuals held by data brokers constitutes a national security risk.“ She warns: „If the bulk of European personal data remains under the control of U.S. companies and opaque data brokers, defending Europe against a Russian attack becomes markedly more difficult.“ She sees „compelling grounds to ban tracking outright and to create a new, privacy respectful advertising ecosystem“.
Team L’Echo: Nicolas Baudoux, Benjamin Verboogen. Team Le Monde: Martin Untersinger, Damien Leloup. Team BNR: Lisanne Wichgers, Bart van Rijswik. Team BR: Katharina Brunner, Rebecca Ciesielski, Maximilian Zierer, Florian Heinhold. Team netzpolitik.org: Ingo Dachwitz, Sebastian Meineck, Maximilian Henning, Anna Biselli, Daniel Leisegang.
Datenschutz & Sicherheit
Windows: Microsoft konkretisiert NTLM-Aus, nennt aber immer noch kein Datum
In einem weiteren Blog-Posting verspricht Microsoft, das Sicherheitsproblem NTLM aus der Welt zu schaffen. „Mit der nächsten Version von Windows Server“ soll es dann so weit sein; wann die erscheint, ist jedoch nach wie vor ungewiss. Aktuell ist NTLM zwar deprecated, aber nach wie vor in vielen Windows-Systemen aktiv und Administratoren müssen die davon ausgehenden Gefahren managen.
Weiterlesen nach der Anzeige
Die Sünden der Vergangenheit
NTLM ist ein seit Jahrzehnten veraltetes Authentifizierungsverfahren, dessen Sicherheitsprobleme altbekannt sind und immer noch etwa von Ransomware-Banden ausgenutzt werden, um sich den Zugang zu Konten mit höheren Rechten zu verschaffen. Insbesondere abgefangene NTLMv1-Hashes lassen sich leicht knacken – etwa mit den von Google bereitgestellten Rainbow-Tabellen. Außerdem lassen sich NTLM-Hashes auch für Pass-The-Hash-Attacken nutzen.
Trotzdem zögert Microsoft, das veraltete Protokoll komplett abzuschalten. Zu viele Systeme nutzen das Verfahren noch. Etwa weil sie keine direkte Verbindung zu einem Domain Controller haben, der für eine Kerberos-Authentifizierung nötig wäre. Oder weil es sich um lokale Accounts handelt oder NTLM fest verdrahtet („hard coded“) ist, erklärt Microsoft. Doch in der zweiten Hälfte des Jahres 2026 will man diese kritischen Punkte der Migration weg von NTLM aus der Welt geschafft haben. IAKerb, lokale Key Distribution Center und Updates zentraler Windows-Komponenten sollen es bis dahin richten.

Mit der nächsten großen Windows-Server-Version soll es kommen, das Abschalten von NTLM
(Bild: Quelle: Microsoft)
Das Ende naht
Und dann soll es endlich so weit sein. Mit der nächsten großen Windows-Server-Version und den zugehörigen Windows-Clients will man NTLM standardmäßig deaktivieren, heißt es jetzt bei Microsoft. Ganz aus der Welt ist es damit jedoch weiterhin nicht, beugt man übertriebenen Erwartungen der Security-Community vor. Der NTLM-Code wird immer noch Teil von Windows bleiben und Admins werden das unsichere Protokoll somit reaktivieren können. Wann man diesen letzten Schritt der Ausmusterung von NTLM vollziehen will, dazu lässt sich der Konzern nicht weiter aus.
Wer für die Sicherheit von Windows-Netzen verantwortlich ist, sollte nicht auf dieses ungewisse Ende warten, sondern vielmehr sofort Maßnahmen ergreifen, um die von NTLM ausgehenden Gefahren einzuhegen. Wie das sinnvoll geht, erklärt etwa das heise security Webinar zum Thema Sicherheitslücken in NTLM und Kerberos verstehen und schließen. Denn auch den designierten NTLM-Nachfolger Kerberos plagen Sicherheitsprobleme, die Angreifer etwa beim Kerberoasting gezielt ausnutzen.
Weiterlesen nach der Anzeige
(ju)
Datenschutz & Sicherheit
Anonymisierendes Linux: Notfall-Update Tails 7.4.1 erschienen
Das Tails-Projekt hat die auf anonyme Bewegung im Netz spezialisierte Linux-Distribution in Version 7.4.1 herausgegeben. Es handelt sich um ein Notfall-Update zum Schließen einer kritischen Sicherheitslücke.
Weiterlesen nach der Anzeige
In der Versionsankündigung der Tails-Maintainer erklären sie, dass in der jüngsten Fassung insbesondere die eingesetzte OpenSSL-Bibliothekt auf aktuellen Stand 3.5.4 gebracht wurde. Die schließt die kürzlich bekannt gewordenen Sicherheitslücken in OpenSSL, von denen die gravierendste unauthentifizierten Angreifern etwa das Einschleusen von Schadcode ermöglicht. „Mithilfe dieser Schwachstellen könnten böswillige Tor-Relay-Server einen Tails-Benutzer deanonimisieren“, erklären die Autoren die potenziellen Auswirkungen der Sicherheitslücke. Sie ergänzen zudem, dass ihnen bislang keine Exploits der Schwachstellen in der Praxis zur Kenntnis gelangt sind.
Die Entwickler haben die Gelegenheit auch genutzt, weitere Softwarepakete der Distribution zu aktualisieren. Der Tor-Client ist in Version 0.4.8.22 an Bord und der Mail-Client Thunderbird auf dem Stand 140.7.0.
Tails 7.4.1: Gelöste und bekannte Probleme
Dabei haben sie ein Problem mit der Gmail-Authentifizierung in Thunderbird ausbügeln können. Beim Öffnen der WLAN-Einstellungen vom Tor-Verbindungsassistenten aus zeigt Tails nun einen drehenden Cursor als Feedback an, dass es gerade daran arbeitet.
Ein bekanntes Problem ist, dass die Homepage des Tor-Browsers fälschlicherweise behauptet, dass Tails 7.4 im Einsatz wäre, selbst nach der Aktualisierung auf Tails 7.4.1 Die Links auf die Release-Notes verweisen zudem ebenfalls noch auf die ältere Fassung. Im Zweifelsfall sollen Interessierte unter „Apps“ – „Tails“ – „About Tails“ (respektive „Über Tails“) aufrufen. Der Dialog zeigt korrekt die aktuell laufende Version an.
Die aktualisierte Tails-Fassung ist wie üblich als Abbild zum Verfrachten auf USB-Stick sowie als ISO-Image zum Brennen auf DVD oder Starten einer VM verfügbar.
Weiterlesen nach der Anzeige
Die Version 7.4 von Tails erschien Mitte Januar. Darin haben die Maintainer die Software auf den aktuellen Stand gebracht und kleine Ärgernisse korrigiert, die zwischenzeitlich auftreten konnten.
(dmk)
Datenschutz & Sicherheit
Medien auf X: Im permanenten Shitstorm
Große Nachrichtensendungen wie die Tagesschau und ZDFheute, aber auch Online-Medien wie Tagesspiegel, Die Zeit und Spiegel sowie Fachmedien wie Legal Tribune Online betreiben weiterhin Accounts auf der Plattform X des rechtsradikalen US-Milliardärs Elon Musk und posten dort aktuelle Inhalte. Sie alle wissen um die Probleme auf der Plattform. Doch sie begründen ihre Aktivität damit, dass sie ihren Qualitätsjournalismus gegen die Desinformation auf X setzen und das Publikum dort abholen wollen, wo es sich aufhält.
Wir haben anhand einer Stichprobe analysiert, wie sich diese Medien auf X schlagen: Wie oft werden die Tweets angesehen, wie oft retweetet, wie interagieren die Nutzer:innen mit den Medien und ihren Inhalten?
Bei der beispielhaften Untersuchung wird klar: Die auf X verbliebenen seriösen Medien befinden sich in feindlichem Terrain. Teils haben sie zwar hohe Followerzahlen, ihre Inhalte werden aber verhältnismäßig wenig Nutzer:innen angezeigt. Wohlwollende Interaktionen wie Retweets können sie kaum generieren. Dafür bläst ihnen in Kommentaren der Wind eisig ins Gesicht.
Gezielter Umbau nach rechts
Für das unwirtliche Klima ist nicht zuletzt Elon Musk selbst mitverantwortlich. Kurz nach dem 44 Millarden US-Dollar schweren Kauf des Online-Dienstes im Jahr 2022 entließ er ganze Moderationsteams und holte im Namen der Meinungsfreiheit zuvor gesperrte Rechtsextremisten, Trolle und professionelle Lügner:innen auf den Dienst zurück. Werbekunden sprangen ab, da sie offenbar ihre Anzeigen ungern neben Nazi-Inhalten sehen wollten. Musk akzeptierte das nicht und überzog die Abtrünnigen mit Klagen.
In diese länger werdende und unvollständige Liste an Kontroversen reiht sich nun der jüngste Skandal um den KI-Chatbot Grok ein. Die ebenfalls zum Firmenimperium Musks gehörende KI-Anwendung ist in X integriert und spuckt auf Anweisung alles mögliche aus – darunter zuletzt auch sexualisierte Deepfakes von Nutzer:innen, in aller Regel von Frauen und sogar von Minderjährigen. Neu ist das Phänomen zwar nicht, aber Grok machte es leicht, bis X doch noch technische Einschränkungen implementierte: Noch nie ließen sich solche Inhalte derart einfach erstellen und an ein globales Publikum ausliefern.
Der Umbau von X zu einer offen rassistischen und sexistischen Plattform geht Hand in Hand mit Musks Unterstützung für rechtsradikale und antidemokratische Bewegungen, hierzulande die AfD. Der Unternehmer macht kein Geheimnis daraus, sein soziales Netzwerk in den Dienst einer rechtsradikalen Revolution zu stellen.
Im Vorjahr zeigte eine Untersuchung von ZDF Frontal, dass die Empfehlungsalgorithmen von X rechte Parteiinhalte überproportional bevorzugen. Bei rassistisch motivierten Ausschreitungen im Sommer 2024 in England hat laut einer Studie von Amnesty International das Empfehlungssystem von X „eine zentrale Rolle“ gespielt. Auch die EU-Kommission vermutet, dass von den algorithmischen Empfehlungen systemische Risiken ausgehen könnten, hat ihre Untersuchungen aber noch nicht abgeschlossen.
Viele haben X verlassen – doch manche sind geblieben
Viele Nutzer:innen, aber auch Medienhäuser und sonstige Organisationen haben deshalb in den vergangenen Jahren die Online-Dienste des rechtsradikalen US-Milliardärs verlassen. Ob Niedersächsischer Landtag, das Jüdische Museum München oder netzpolitik.org, die Gründe für den Rückzug ähneln sich: X sei ein Ort der Zensur, des Rassismus, Antisemitismus und des rechten Agendasettings geworden, begründeten Dutzende Abgeordnete, Wissenschaftler:innen und Journalist:innen im Winter 2024 ihren Abgang. Zwar nutzen in Deutschland immer noch rund sieben Millionen Menschen monatlich die Plattform, ihre Reichweite geht jedoch europaweit kontinuierlich zurück.
Warum also bleiben weiterhin manche Medien auf X und versorgen das soziale Netzwerk mit Inhalten, die wiederum dessen Attraktivität steigern?
Auch hier ähneln sich die Gründe: So betont etwa Markus Sehl, stellvertretender Chefredakteur von Legal Tribune Online (LTO), Beiträge über zahlreiche Social-Media-Kanäle auszuspielen, darunter Instagram, LinkedIn, Bluesky, Facebook – und eben auch X. „Wir verbinden mit unserer Präsenz auf allen diesen Plattformen das Ziel, mit unseren Inhalten dort ein seriöses Inhaltsangebot zu machen. Eines, das Filterblasen durchdringt, für konstruktive Irritation sorgt und schließlich einen demokratischen Diskurs ermöglicht“, so Sehl auf Anfrage von netzpolitik.org.
Bescheidene Reichweite, bescheidene Debatten
Wir haben dieses hehre Ziel einem Realitäts-Check unterzogen. In unserem Beobachtungszeitraum wurden Tweets des juristischen Fachmediums, allesamt mit Links zu LTO-Artikeln, laut der Statistikanzeige von X am Tag der Postings durchschnittlich nur 1.329 Mal von Nutzer:innen gesehen. Derzeit folgen mehr als 28.000 Accounts dem X-Auftritt von LTO. Sonderlich viel Aufmerksamkeit oder gar „demokratischen Diskurs“ konnten die Postings nicht entfachen. Im Schnitt wurden die Tweets knapp mehr als fünf Mal retweetet und zwölf Mal mit einem Herzchen versehen („geliked“). Die Hälfte der untersuchten Postings erhielt keine Antwort, im Schnitt waren es 2,2 Antworten („replys“) pro Tweet.
Und wie sieht es mit der Qualität der Antworten aus? Nennenswerte Diskussionen lösten LTO-Tweets über die Sabotage der russischen Öl-Pipeline Nord Stream aus, über das ungarische Gerichtsverfahren gegen die non-binäre Aktivist:in Maja T. oder ein Beitrag zur Mediendebatte über Inhaltemoderation und Algorithmenregulierung.
Dass solche Themen besonders viel Aufmerksamkeit auf X nach sich ziehen, ist so erwartbar wie viele der Antworten darunter: „Das sind Taschenspielertricks um unliebsame Meinungen kleinzumachen und das weiß auch der Autor der polarisieriende Ausagen mit Desinformationen vermengt“, polterte etwa ein gewisser Leo gegen Schleswig-Holsteins Ministerpräsidenten Daniel Günther (CDU) sowie den Autor des LTO-Artikels.
Schnittstellen-lose Stichprobe
Eine massenhafte Auswertung der jeweiligen X-Auftritte deutscher Medien ist nicht mehr ohne Weiteres möglich, seit Elon Musk die dazu notwendigen Schnittstellen hinter eine Bezahlschranke gepackt hat. Für unsere kleinere Untersuchung haben wir deshalb am 19. Januar 2026 jeden zweiten Tweet eines Mediums erfasst, bis insgesamt zehn erfasste Postings zusammengekommen waren. Diese zehn Tweets pro Medium haben wir hinsichtlich Views, Replys, Retweets und Likes ausgewertet. Außerdem haben wir uns angesehen, ob die Medien selbst in den Replys angegriffen werden und haben die Reaktionen auf die Tweets qualitativ bewertet.
Aufgrund des kleinen Ausschnitts können die erhobenen Daten nur als Stichprobe gelten, die aber deutliche Muster aufzeigt. Diese konnten wir auch bei Tweets außerhalb des Untersuchungszeitraums finden.
Grundsätzlich sind die Zahlen mit Skepsis zu betrachten, nicht nur wegen der kleinen Stichprobe. Manipulationsversuche sind seit Jahren nicht mehr aus dem Internet wegzudenken. Doch wozu noch vor nicht allzu langer Zeit umfangreiche Troll-Farmen notwendig waren, lassen sich Aufruf- und Engagement-Metriken in Zeiten von ChatGPT, Grok und anderen KI-Chatbots mit deutlich weniger Aufwand und raffinierter verfälschen.
Ganze Schwärme von KI-Bots, die etwa über Online-Dienste hinweg authentisches Handeln und konsistente Persönlichkeiten vortäuschen können, überfluten derzeit soziale Medien, warnten zuletzt mehrere Studien. Oft ist nur schwer erkennbar, ob hinter Postings echte Menschen oder Propagandabots stecken. „Die Verschmelzung von agentenbasierter KI und LLMs markiert eine neue Grenze im Informationskrieg“, führt eine der Studien aus.
Ähnliche Vorsicht ist auch bei der Anzeige der Views oder der Followerzahlen angebracht. Nicht einmal X dürfte einigermaßen verlässlich über verdächtige Aktivitäten auf dem eigenen Dienst Bescheid wissen, seit Musk die dafür zuständigen Teams dramatisch reduziert und zugleich die Moderationsregeln gelockert hat – wenn die Manipulationsversuche nicht gleich aus dem eigenen Haus kommen.
Konzentrierter brauner Sumpf
Das bei LTO beobachtete Phänomen lässt sich auch bei anderen noch auf X aktiven Medien feststellen. Kaum Reichweite, wenig Engagement von Nutzer:innen, und wenn es Antworten unter den Tweets gibt, enthalten diese nur selten erhellende Einsichten. Im Gegenteil: Oft genug besetzen reaktionäre Trolle den Platz, den es ohne die Tweets der Medien-Accounts so nicht gegeben hätte. Dabei kapern sie die Debatte und posten gerne auch themenfremde und beliebige Links zu rechtsradikalen Aufregerthemen. Außer einem braunen Sumpf bleibt oft nicht viel übrig unter den Tweets der Medien.
So folgen dem X-Account von Die Zeit derzeit rund 2,3 Millionen Accounts. Einzelne Postings wurden im Beobachtungszeitraum trotz dieser auf dem Papier großen Zahl durchschnittlich nur knapp 2.900 Mal angesehen, 2,1 Mal retweetet, 5,1 Mal geliked und 4,1 Mal beantwortet. Mehrere Tweets erhielten zum Zeitpunkt der Auswertung gar keine Reaktion, die meisten Antworten (17) liefen bei einem Tweet über ein internes Papier der Grünen zur EU-Außenpolitik auf. Ein gefundenes Fressen für selbsternannte „Parodieaccounts“, die die Schuld für jedwedes Problem bei den Grünen verorten.
Bemerkenswert ist, was passiert, wenn der Zeit-Account zuweilen gezielt ein bestimmtes Publikum anzusprechen scheint. Ein Tweet über die Fußballbundesliga erwähnt etwa den rechtsextremen AfD-Spitzenpolitiker Tino Chrupalla. Wie auch im Anreißer des Originalartikels steht dort, der AfD-Politiker habe „nicht viel verpasst“. Dafür gab es Kritik: „Warum wird dieser Faschist hier einfach so erwähnt?“, fragte immerhin ein:e Nutzer:in mit einer EU-Flagge im Profilbild. Wenig später wird der Account selbst als Faschist beschimpft.
In einem anderen Tweet schien die Zeit-Redaktion Gratis-Werbung für die österreichische FPÖ zu machen: Ein von der Rechtsaußen-Partei neu gestarteter Radiosender sei „sehr langweilig (…) und gerade deshalb interessant – besonders für deutsche Hörer“. Was auch immer die Motivation hinter diesen anbiedernden Anreißern war, der Erfolg hielt sich in Grenzen. Beide Tweets erhielten insgesamt nicht einmal zehn Antworten – zusammengerechnet. Als Reibebaum, der Engagement und Klicks lostritt, eignet sich diese Form der Ansprache offenbar nicht.
Gegengewicht oder Zielscheibe?
Auch Zeit Online begründet ihren Verbleib auf X damit, ein Korrektiv sein zu wollen. „Unser Ziel ist es, verlässliche Informationen und unabhängigen Journalismus möglichst vielen Menschen zugänglich zu machen“, teilt eine Verlagssprecherin mit. Die Zeit sei „ein Gegengewicht zur aggressiven, wenig produktiven Diskussionskultur und der Zunahme von Desinformation auf X, weshalb wir unseren Account mit 2,3 Millionen Followern zum jetzigen Zeitpunkt weiterhin betreiben. Neben X sind wir auf Plattformen wie Bluesky, Threads und WhatsApp aktiv und bauen diese Kanäle weiter aus“, heißt es aus dem Verlag.
Ein Stückchen erfolgreicher ist der X-Account des Spiegel. Im Untersuchungszeitraum abgesetzte Tweets huschten im Schnitt rund 4.200 Mal über die Bildschirme der Nutzer:innen. Unterm Strich erhielten sie je knapp elf Antworten, 3,6 Retweets und rund 9 Likes. Allerdings verzerrt ein Ausreißer das Bild: Ungewöhnlich viel Resonanz erhielt ein Retweet des @SPIEGEL_EIL-Accounts, der staatliche Förderung von Elektroautos zum Thema hatte. Zum Zeitpunkt der Erfassung konnte der Tweet über 12.000 Views verzeichnen, rund eine Woche später ist die Zahl auf 22.000 angestiegen. Rechnet man diesen Tweet heraus, sinkt die Anzahl der durchschnittlichen Views auf rund 3.000. Für ein angebliches Millionenpublikum – @derspiegel hat über 3 Millionen Follower, @SPIEGEL_EIL über 1,5 Millionen – ist das eine magere Ausbeute.
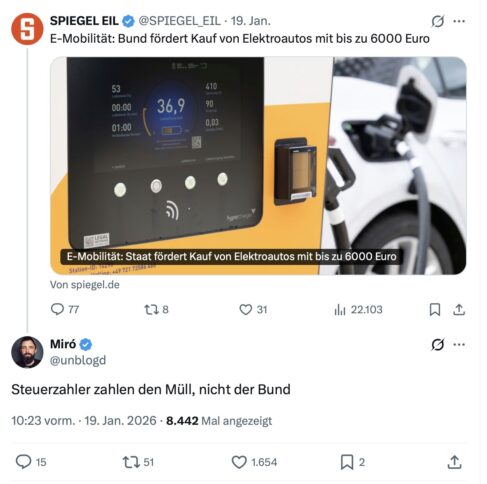
Präsenz schafft Diskursräume für Rechtsradikale
Welche Diskursräume die Tweets erst schaffen, zeigt erneut ein Blick in die Antworten unter diesen. Bei besagtem E-Auto-Tweet spülte das Empfehlungssystem von X den rechten Influencer Miró Wolsfeld ganz nach oben. „Steuerzahler zahlen den Müll, nicht der Bund“, wetterte der auch als Unblogd bekannte Aktivist. Während der Tweet des Spiegels gerade mal 8 Retweets und 31 Likes bekommt, holt sich Wolsfeld 51 Retweets und 1.654 Likes mit seinem Kommentar ab. Auch solche Phänomene sind ein klares Zeichen, wer das Sagen auf der Plattform hat.
Ein solches Auftreten lässt sich auf X inzwischen monetarisieren. Dem Account kann man freiwillig für 3,33 Euro im Monat folgen, den zahlenden Followern verspricht Wolsfeld als Bonus „Demnächst Podcasts vorab“. Gekoppelt an Empfehlungsalgorithmen, die umstrittene Inhalte bevorzugen, um damit Nutzer:innen länger auf dem Dienst zu halten, entsteht ein perverses Anreizsystem: Es belohnt diejenigen, die mit reißerischen Inhalten möglichst viel Aufmerksamkeit erregen.
Mit Spott und Hohn wird dabei oft nicht gespart. „SPIEGEL, STERN, SZ, usw. haben auf X einfach so gut wie nichts mehr zu melden“, tönte der rechte Influencer vor wenigen Tagen. „Bei der üblich hohlen Propaganda gibt es so gut wie keine Likes auf deren Posts, dafür aber etliche Kommentare, die den Nonsens zerlegen. Der Wind hat sich hier definitiv gedreht.“
„Wichtige Kontaktpunkte“ zu wem?
Für seriöse Medien, die weiterhin auf X bleiben und der Plattform Inhalte zuliefern, steigt tatsächlich der Druck. „Wenn wir mit den redaktionellen Inhalten unserer Medienmarken neue Nutzerinnen und Nutzer erreichen wollen, müssen wir dorthin gehen, wo sie sich informieren, und das sind eben oft Plattformen, die weniger offen und verantwortungsvoll sind, als wir uns das wünschen“, teilt eine Spiegel-Sprecherin mit.
„Wenn sich unabhängige Medien von diesen Plattformen selbst ausschließen, verlieren wir wichtige Kontaktpunkte zu unseren Zielgruppen. Und an der Nutzung der Plattformen würde sich durch den Rückzug der Qualitätsmedien nichts ändern“, sagt die Sprecherin.
Doch dass sich der Wind gedreht hat, ist auf X kaum von der Hand zu weisen. Die Plattform ist unter den Tweets der Accounts großer deutscher Medien fest in der Hand von Rechtsextremen, Zynikern, Rassisten und Menschen, die einfach nur ihrem Hass auf klassische Medien und die Welt freien Lauf lassen.
Hohes Vertrauen in öffentlich-rechtliche Medien
Diese Wut trifft insbesondere öffentlich-rechtliche Medien. Im öffentlichen Auftrag sollen sie dazu beitragen, die Menschen in Deutschland umfassend und ausgewogen zu informieren. Deshalb landen sie immer wieder im Visier von Rechtsextremen wie dem AfD-Politiker Björn Höcke, der etwa die Medien-Staatsverträge aufkündigen will. Von ganz rechts bis in die Bundesregierung hinein wird am öffentlich-rechtlichen Rundfunk gesägt.
Trotz aller Versuche, die Glaubwürdigkeit öffentlich-rechtlicher Medien zu untergraben, genießen die Sender bis heute verhältnismäßig viel Vertrauen in der Bevölkerung, mehr als private Tageszeitungen oder Sender. Zwei Drittel der Befragten hielten den öffentlich-rechtlichen Rundfunk (ÖRR) für „unverzichtbar“, wie eine repräsentative Studie im Vorjahr ergab. Den parteiübergreifenden Konsens durchbrechen lediglich Anhänger:innen der Kleinpartei BSW sowie der AfD, die den sogenannten Systemmedien überwiegend nicht vertrauen.
Viele Follower, wenige Ansichten
Unsere Auswertung zeigt, dass sich die Bedeutung der Öffentlich-Rechtlichen auch im Internet abbildet. So wurden die Tweets der großen Kanäle @tagesschau (5,1 Millionen Follower) und @ZDFheute (1,3 Millionen Follower) deutlich mehr Menschen in der App und auf der Seite von X angezeigt als die Postings privater Medien. Im Beobachtungszeitraum sahen im Schnitt rund 24.000 Nutzer:innen Tweets der Tagesschau, bei ZDFheute waren es rund 23.000. Angesichts der hohen Followerzahlen der Kanäle sind diese Zahlen jedoch mehr als ernüchternd.
Wie viele der Nutzer:innen tatsächlich auf einen Link in einem Tweet klickten, verrät X nicht. Und auch die sogenannten Referrer-Zahlen von tagesschau.de und ZDFheute, die mehr über die Herkunft der Besucher:innen verraten, liegen uns nicht vor. Schätzungen von Marketing-Firmen gehen bei X von einer Klickrate von etwa einem Prozent auf externe Links aus.
Wir sind communityfinanziert
Unterstütze auch Du unsere Arbeit mit einer Spende.
Warum die beiden Kanäle der Öffentlich-Rechtlichen laut der nicht notwendigerweise zuverlässigen Views-Anzeige von X derart besser abschneiden als Spiegel oder Die Zeit, geht aus den Daten nicht hervor. Klar ist aber, dass X seit der Übernahme von Musk Tweets mit Links benachteiligt werden, dafür sprechen unterschiedliche Untersuchungen und Berichte.
Zudem hat X schon im Jahr 2023 durch das Design der Tweets Links in die Außenwelt unattraktiver gestaltet, indem nicht mehr die Vorschau eines Artikels eingebettet wird. Hintergrund ist, dass X wie auch andere Big-Tech-Plattformen versucht, die Nutzer:innen auf der Plattform zu halten und dort „Engagement“ und damit Werbeabspielungen zu erreichen. Nutzer:innen über einen Klick auf andere Seiten im Netz zu schicken, widerspricht diesem Ziel.
Tagesschau und ZDFheute sehen sich als Gegenpol
Laut einem Sprecher der ARD geht es der Tagesschau darum, „seriöse und verifizierte Nachrichteninhalte Nutzenden auf Social-Media-Plattformen zur Verfügung zu stellen und damit einen Gegenpol zu Desinformationen und Verschwörungsmythen zu setzen.“ Dies gelinge mit Blick auf die Zugriffszahlen, die die Artikellinks der Tagesschau auf X erzielten, „weiterhin in relevanter Größenordnung“.
Angesichts der relativ zur hohen Followeranzahl wenigen Views und der geschätzten Klickrate von einem Prozent dürfte sich der Anteil von X bei den 50 bis 80 Millionen monatlichen Seitenbesuchen auf tagesschau.de in Grenzen halten. Zur Einordnung: Auch vor Elon Musks Übernahme erreichte beispielsweise netzpolitik.org mit seiner damals Twitter-affinen Leser:innenschaft nie mehr als ein bis zwei Prozent aller Seitenabrufe über die Plattform. Diese Zahlen umfassen sowohl Klicks auf Links in Tweets des eigenen Accounts als auch in Tweets anderer.
ZDF schreibt gegenüber netzpolitik.org, dass alle Social-Media-Aktivitäten einem „kontinuierlichen Controlling mit Blick beispielsweise auf Zielgruppe, Performance und Entwicklung der jeweiligen Plattform“ unterliegen würden. „Sollten Accounts entsprechende Ziele nicht erreichen bzw. genannte Kriterien nicht erfüllen, werden diese eingestellt.“
Was für Ziele das sind, gibt das ZDF nicht preis, führt jedoch aus, warum man weiter auf der Plattform poste: „Das Nachrichtenangebot ZDFheute veröffentlicht aktuelle Informationen weiterhin auf X, um Qualitätsjournalismus auch dort möglichst vielen Menschen einfach zugänglich zu machen.“
Doch die Versuche der Tagesschau und von ZDFheute werden von den Nutzenden auf der Plattform X wenig honoriert. Das Gegenteil ist der Fall. Dementsprechend heiß geht es in den Kommentaren unter den Tweets zu: Durchschnittlich liefen bei der Tagesschau 77 Kommentare auf, bei ZDF Heute sogar 100.
Dort findet eine Schlacht um die Deutungshoheit statt. Mit 173 Kommentaren besonders umkämpft war ein Tweet zu einer Eilmeldung, dass der Begriff „Sondervermögen“ zum Unwort des Jahres 2025 gewählt wurde. Die Debatte lenkten dem rechten Milieu zuordnenbare Accounts, etwa der des rechten Magazins Krautzone. Eine der Top-Antworten wollte etwas ganz anderes diskutieren: „Für mich ist ‚ÖRR‘ das Unwort des Jahrhunderts.“
Öffentlich-rechtliche Medien im Dauer-Shitstorm
Die grundsätzliche Feindseligkeit der Rezipient:innen auf X ist bei den untersuchten Medien am Verhältnis von Antworten zu Retweets erkennbar, der „Reply Retweet Ratio“. Tweets mit vielen Replys und wenigen Retweets zeigen in der Regel eine Kontroverse oder eine Ablehnung der Nutzer:innen an. Diese kann sich auf den Inhalt des Tweets oder auf den Postenden selbst beziehen.
Es ist ganz normal, dass einzelne Tweets bisweilen mehr Replys erhalten als Retweets. Ungewöhnlich ist aber, dass bei den öffentlich-rechtlichen Nachrichten-Accounts von Tagesschau und ZDFheute mehr Replys als Retweets der Regelfall sind. Die Tagesschau erhielt im Untersuchungzeitraum drei Mal so viele Replys wie Retweets, ZDF gar fast vier Mal soviele. Auch der Spiegel erhielt drei mal so viele Replys wie Retweets, bei der Zeit waren es immer noch doppelt so viele. Einzig LTO war als Medium nicht so negativ im Fokus – es erreichte mehr Retweets als Replys.
Bei ZDFheute und Tagesschau gab es in den untersuchten Tweets bis auf eine Ausnahme unter jedem Tweet direkte Angriffe auf die Sendungen oder die Sender selbst, oft auch mehrfach. Dabei ging es in den Kommentaren nicht um sachliche oder inhaltliche Kritik an Nachrichteninhalt oder dessen Aufbereitung.
So findet man unter Tweets regelmäßig die Forderung, die Pflicht zum Rundfunkbeitrag abzuschaffen. Die Tagesschau wird unter anderem als „Terrorpropaganda“, „Propagandascheisse“ oder „Schundfunk“ diffamiert, das ZDF als „Schrottsender“ und die ZDFheute-Redaktion sieht ein User als heroinabhängig. Das ist nur ein kleiner Ausschnitt dutzender Beschimpfungen, die wir als Reaktion auf das kleine Set an untersuchten Tweets identifizieren konnten.
netzpolitik.org holt auf Bluesky mehr Retweets als Tagesschau, heute, Spiegel und Zeit zusammen
Wir haben uns zum Vergleich angesehen, wie die Interaktion beim Account von netzpolitik.org auf Bluesky aussieht. Im gleichen Untersuchungszeitraum erhielt netzpolitik.org auf Bluesky eine deutlich umgekehrte Reply-Repost-Ratio: Fast neun Mal mehr Accounts klickten auf den Repost-Button als auf Reply. Mehr Reposts als Replys sind der eigentliche Normalzustand bei Diensten wie X, Bluesky oder Mastodon.
Spannend war auch die Anzahl der Reposts insgesamt beim Account unserer Redaktion auf Bluesky. Der Account von netzpolitik.org mit seinen etwa 35.000 Followern erreichte im Untersuchungszeitraum am 19. Januar mit 755 Reposts mehr Verstärkung als Tagesschau, Heute, Spiegel, Zeit und LTO auf X mit ihren fast 12 Millionen Followern. Insgesamt kamen diese Accounts auf 615 Reposts. Und das, obwohl den untersuchten Medien auf X mehr als 300 Mal mehr Accounts folgen.
Weder Tagesschau noch ZDFheute betreiben einen offiziellen Kanal auf Bluesky. Die Sender ARD und ZDF sind jedoch auf Mastodon vertreten und betreiben dort jeweils eigene Server.
Überprüfen, bis das Fass überläuft
Ein Abschied von X fällt offenkundig nicht leicht. Das Bleiben aber auch nicht. „Die Entwicklung und die gesellschaftlichen Auswirkungen von X beobachten wir kritisch und diskutieren regelmäßig, ob und wie wir dort weiterhin präsent sein sollten“, heißt es von Die Zeit. „Fehlentwicklungen auf Plattformen nehmen wir ernst, selbstverständlich behalten wir die Entwicklungen gerade bei X kritisch im Blick“, beteuert LTO. Auch der Spiegel befasse sich im Lichte der neuen Erkenntnisse „erneut mit unserer Präsenz auf der Plattform“, sagt eine Sprecherin. Die Antworten ähneln denen der EU-Kommission, der Bundesregierung, Parteien im Bundestag und Ministerien, die weiterhin der Plattform treu sind und immer schwerer Argumente dafür finden.
Es bleibt also spannend, wann der Punkt erreicht ist, an dem es auch für die letzten Verbliebenen nicht mehr weiter geht. Die Erfahrungen der letzten Jahre zeigen: Der Skandal mit sexualisierten Deepfakes realer Personen rund um den X-Chatbot Grok wird nicht der letzte bleiben.
-

 Entwicklung & Codevor 3 Monaten
Entwicklung & Codevor 3 MonatenKommandozeile adé: Praktische, grafische Git-Verwaltung für den Mac
-

 Künstliche Intelligenzvor 1 Monat
Künstliche Intelligenzvor 1 MonatSchnelles Boot statt Bus und Bahn: Was sich von London und New York lernen lässt
-

 Apps & Mobile Entwicklungvor 2 Monaten
Apps & Mobile Entwicklungvor 2 MonatenHuawei Mate 80 Pro Max: Tandem-OLED mit 8.000 cd/m² für das Flaggschiff-Smartphone
-

 Apps & Mobile Entwicklungvor 2 Monaten
Apps & Mobile Entwicklungvor 2 MonatenFast 5 GB pro mm²: Sandisk und Kioxia kommen mit höchster Bitdichte zum ISSCC
-

 Entwicklung & Codevor 2 Monaten
Entwicklung & Codevor 2 MonatenKommentar: Anthropic verschenkt MCP – mit fragwürdigen Hintertüren
-

 Social Mediavor 2 Monaten
Social Mediavor 2 MonatenDie meistgehörten Gastfolgen 2025 im Feed & Fudder Podcast – Social Media, Recruiting und Karriere-Insights
-

 Datenschutz & Sicherheitvor 2 Monaten
Datenschutz & Sicherheitvor 2 MonatenSyncthing‑Fork unter fremder Kontrolle? Community schluckt das nicht
-

 Künstliche Intelligenzvor 3 Monaten
Künstliche Intelligenzvor 3 MonatenWeiter billig Tanken und Heizen: Koalition will CO₂-Preis für 2027 nicht erhöhen







